Our Solution
 CoreGuard Overview
CoreGuard Overview
CoreGuard® is the first to fill the enforcement layer of the cybersecurity stack. It is the only solution that prevents the exploitation of software vulnerabilities and immunizes processors against entire classes of network-based attacks.
CoreGuard silicon IP integrates with all RISC architectures to provide separate, sentry logic that acts as a bodyguard to protect embedded systems from cyberattacks. It monitors every instruction executed by the host processor to ensure that it complies with a defined set of security, safety, and privacy rules. If an instruction violates an existing rule, CoreGuard stops it from executing before any damage can be done.
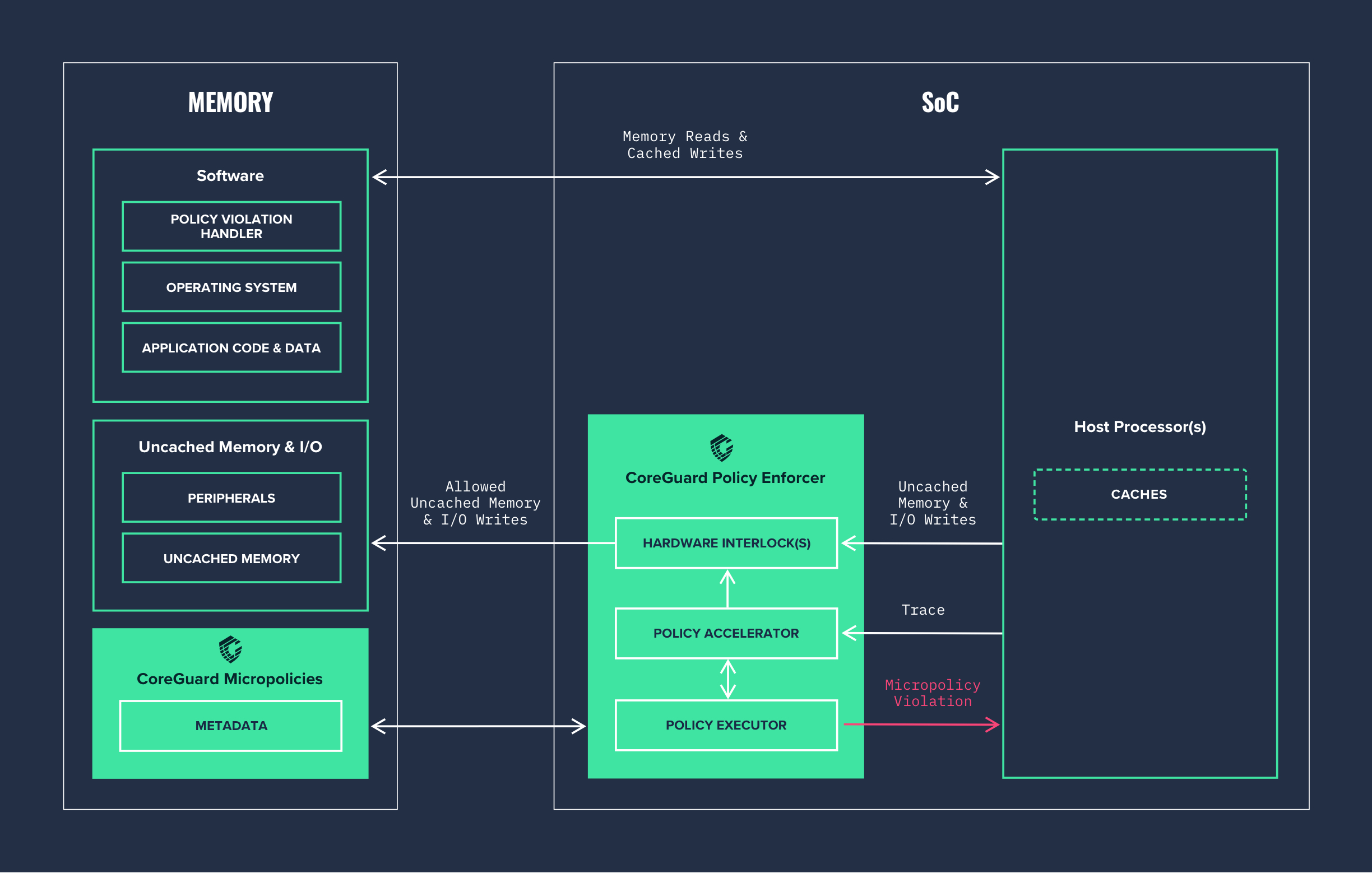
How It Works
CoreGuard provides protection at the lowest possible level by using a hardware interlock. The hardware interlock controls the communication between the host processor and the outside world to ensure nothing is sent out peripherals without first being verified by the CoreGuard Policy Enforcer.
Updatable security, safety, and privacy rules, called micropolicies, are installed on the SoC. They give CoreGuard information it needs to distinguish between good and bad instructions. CoreGuard collects application information usually discarded by the compiler to create identifiable metadata about every piece of data, and every instruction, executed by the host processor.
The CoreGuard Policy Executor (PEX) crosschecks the metadata of every instruction against an installed set of micropolicies. If an instruction violates an existing micropolicy, CoreGuard issues a violation and stops it from executing before any damage can be done. If there is no micropolicy violation, the host processor executes the instruction normally.
 Download Diagram
Download Diagram
At the Core of CoreGuard
-
RulesMicropoliciesMicropolicies define security, safety, and privacy rules that enable CoreGuard hardware to determine which instructions to execute and which to block. Micropolicies are designed to stop entire classes of attacks, including buffer overflows, code injection, data exfiltration, and even safety violations.
-
InformationMetadataCoreGuard maintains metadata for every piece of data and every instruction that is handled by the host processor. The combination of micropolicy rules and metadata is what gives CoreGuard the knowledge it needs to make informed decisions about the safety of each instruction the host processor attempts to execute.
-
EnforcementHardwareThe Policy Enforcer is CoreGuard’s hardware mechanism for monitoring and protecting the host processor. It is implemented as part of the processor’s silicon design, and it enables CoreGuard to check every instruction for compliance with micropolicies. When an instruction violates a micropolicy, the Policy Enforcer blocks it from executing.
Micropolicies
CoreGuard micropolicies are designed to stop entire classes of attacks—not just specific attacks. Because of this, CoreGuard can dynamically block malicious behaviors from both known and unknown sources, and can even defend against zero-day attacks that exploit software vulnerabilities unknown to the software maker or user.
CoreGuard comes with a base set of micropolicies that together can stop the the most prevalent and severe network-based attacks—with absolutely no alteration to your application.
Included with CoreGuard
Heap
Function: Enforces protection on heap blocks in memory
Type of Attacks: Stops buffer overflow and overread attacks
Stack
Function: The Stack micropolicy enforces control flow integrity by protecting control data, including the return address, stored on the stack
Type of Attacks: Stops buffer overflow and overread attacks
RWX
Function: Establishes traditional Read/Write/Execute permissions for code and data, but with a fine-grained resolution
Type of Attacks: Stops code injection attacks
Customizable Protection Level
For even more protection, you can layer additional micropolicies on top of the base set, or work with us to create custom micropolicies that meet the unique security, safety, and privacy requirements of your systems. The result is fine-grained protection against cyberattacks, flawed software, device malfunctions, and safety violations.
The CoreGuard Advantage

Immunizes Processors
Real-time Attack Detection
Unassailable Silicon
Cross-platform Security
Customizable & Updatable
Security Stack Protection
How It’s Delivered
When you sign a Design License for CoreGuard you receive two distinct deliverables.
CoreGuard SDK
The CoreGuard SDK includes an operating system based on the FreeRTOS kernel (a real-time operating system kernel ideal for embedded systems applications). The SDK also includes an embedded systems software simulator, compiler toolchain, a base set of CoreGuard micropolicies, sample applications, and technical documentation.
CoreGuard Policy Enforcer
The CoreGuard Policy Enforcer RTL is licensed and delivered as a set of hardware system Verilog design files. It can include custom modifications specific to each customer’s desired processor, such as pipelining to fit performance and area targets, or custom processor extension support. We provide full integration support and RTL instantiation consultation Get CoreGuard