Resource Center
Webinars
Cyberattack Examples

German Steel Mill Cyberattack
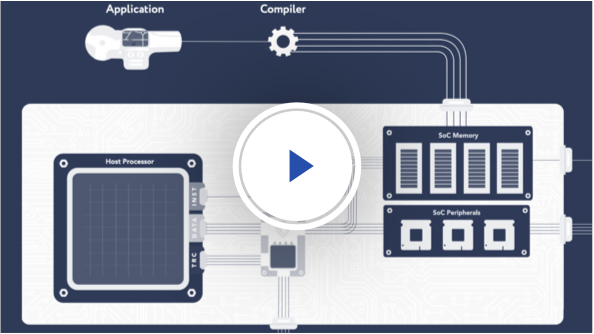
CoreGuard ensures the safe and proper functioning for safety-critical systems

Operation Soft Cell Cyberattack
CoreGuard protects critical infrastructure from corruption or highjacking